TCP is a very important protocol in the Internet. More than half of the traffic in Internet uses TCP. When it comes to reliable communications, TCP plays a major role, let it be logging into Facebook or opening a website like Wikipedia.com the underlying protocol which takes care of these reliable connections is TCP. TCP’s dominance over internet has its advantages and disadvantages from security point of view. The architecture of TCP/IP protocol suit doesn’t have any security features in built, what it has are algorithms for protocol timers, error correction, flow control, buffering, but there is nothing in code for its security, as Internet evolved the techniques to use it in unethical ways also evolved.
These techniques are nothing but the exploitation of vulnerabilities found in the protocol architecture or the way it functions, so what are those? Before we see them, let us have a brief look at a TCP packet header.
These techniques are nothing but the exploitation of vulnerabilities found in the protocol architecture or the way it functions, so what are those? Before we see them, let us have a brief look at a TCP packet header.
 |
TCP along with its unreliable cousin UDP lies in the Transport layer of TCP/IP model (also called as DoD model)
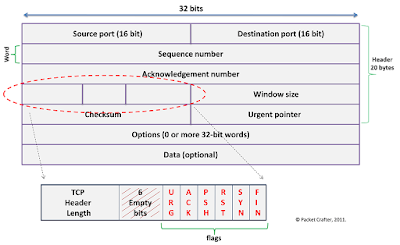
TCP Packet structure:
- TCP Packet = TCP Header (20 bytes) + DATA (max of 65,495).
- Number of words (w) is included in the TCP Header length (n) = w x n = 20byte.
- In the above packet = 32 x 5 = 160bits /8 = 20bytes (default word length = 32bit)
- The size of header indicates the start of the data.
- Sequence and Acknowledge numbers are both 32bit in size.
- The dashed lines between TCP Header and flags are empty 6bits and are not used.
- Next to the empty 6bits are 1bit flags.
- Flags field:
- URG – Urgent Flag
- ACK – Acknowledge Flag
- PSH – Push Flag
- RST – Reset Flag
- SYN – Sync Flag
- FIN – Finish Flag
- Window size indicates the available buffer memory in the stack for communication.
- Checksum is used to calculate the integrity of the TCP Segment
- Urgent pointer is used along with the URG flag. It tells the receiving end where exactly the priority ends for the Data.
- Options field includes few more parameters.
- Data field is where the actual data/payload from the upper layers are stored.
Before we start studying about Flags let us see how they’ll look when captured in a packet analyzer like Wireshark.
The markings in the above picture are the flags in a TCP header.
Now, let have a look at each one of them-
URG –
Urgent flag, very less used in today's protocols, tells the receiving end about a priority data in the TCP segment. This flag is set along with the Urgent Pointer which tells when the priority ends for the data in the segment.
- Example: Best scenario is executing commands on a remote machine using Telnet client. The input of a command through Telnet client should be sent immediately with the commands intact, in order to accomplish this the data transferred to the remote machine will have the URG flag set to 1. But by any chance if the output takes time on the Telnet console then there has to be some kind of latency in the network or the remote machine is having some issues.
- Exploit: This can be used for malicious activities too, but this is used along with the other flags set.
ACK –
Acknowledge flag is used to acknowledge a received SYN packet. ACK flag is set to 1 on the reply packet to the requesting machine. This is just a confirmation sent to the requesting machine that your SYN request has been received. In the initial stage of 3-way handshake the Window size is set to zero. Windowing plays one of the key role in efficiency.
- Exploit: Mostly this flag is used along with the other flags, to use it alone I would think of a silly DoS flooding, where we can send crafted packets with only the ACK flag set, destination/target machine would do nothing but drop them as it won't match with any entries in its state table, unnecessarily using the CPU resources.
PSH –
Push flag is used to push the data without any intermediate buffering(storing). In a TCP header if the PSH flag is set to 1 then it will not be buffered at any intermediate nodes, It will be simply pushed into the network without any intermediate buffering.
- Examle: Mostly PSH flag is set for communications where there shouldn’t be any interruption, like multimedia streaming, executing mission critical database queries, ATM transactions and so on.
- Exploit: Since the data in transit isn't buffered, it is simply pushed to the top application layers for processing. This is one of the key factor in some attacks. In a typical case, an IDS is placed in the intermediate position of the service requesting machine and the service providing machine. IDSs have significant amounts of buffer memory for storing and analyzing the incoming data before sending them to the destination machine. So if a hacker crafts a batch of TCP flags where the PSH flag is set to 1 they might easily bypass an IDS without getting detected or processed, eventually delivering the malicious payload to the application layer.
RST –
Reset flag is used to reset/teardown an existing/established TCP session.
- Example: When a service is running on a network port, like say http on port 80, it runs its corresponding application service. When a remote machine tries to access this service it initially establishes a TCP connection to this port using 3-way handshake. If let's say the http service is stopped on this port, it interrupts the connection and acknowledges to the requesting machine with a TCP RST flag set to 1. Another situation is when we are actively working on, for example a Telnet session, and if by mistake if we close the telnet window the telnet service on the host machine’s port 23 will stop and it immediately sends a TCP with RST flag set to 1 and once the remote machine receives this, it will tear down the connection without any delay or acknowledgement.
- Exploit: What if a hacker wants to scan a remote machine for its open ports/services or to at least to check whether the machine is alive or not? He/she simply sends crafted TCPs to all the well know ports from 0-1023 and-
- if any of them are open they will send a SYN+ACK (acknowledge) which clearly tells the hacker that the port is open and its corresponding service is running.
- If the service is stopped but the port is open it'll send RST packet (acknowledge) which tell the hacker that the service is not running but the port is open.
- If a port is filtered/closed (through firewall) the hacker gets no acknowledgement of any kind, which tells him/her that port is unavailable.
- If the hacker haven’t received any kind of acknowledgements from the target machine on any of its ports then it means that the remote machine is either down or there could be something blocking the connection all together.
- The above points are some of the fundamental principles used in the port scanners like nmap.
SYN –
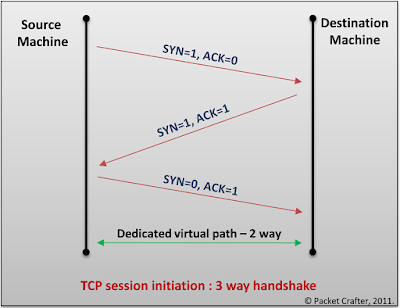
SYN flag is the well know flag in TCP and is used to initiate a TCP session. Before the actual data starts to flow, a TCP segment with 0 data bytes are sent to the remote machine with the SYN flag set to 1, after the three way handshake a dedicated session is established between the source machine to the target machine for the actual data to transfer.
- Example: When we open any website the first step done by the TCP protocol is sending a SYN packet (though initially a DNS query is sent for the name resolution). And once a session is established then the data starts flowing, eventually presenting us with the website, considering that it is available. Anything can go wrong in this transmission, in such cases we might get several errors/messages on the browser based on the nature of the issue. A simplified 3-way TCP handshake is shown below.
- Exploit: Well, why would a malicious hacker open a webpage? if his/her intention is to crash it he/she crafts a batch of TCP segments with the SYN flag set to 1 and with a spoofed IP address like say A.A.A.A, as the source IP, where the machine sending it has an actual IP of let's say B.B.B.B. These packets are sent to a destination machine C.C.C.C which runs a website for example. Once C.C.C.C receives the SYN packets from B.B.B.B, will it be from B.B.B.B? or from A.A.A.A? As the source IP is crafted to show A.A.A.A, destination/target sees the packets as if they're coming from A.A.A.A and sends SYN+ACK to A.A.A.A which doesn’t exist. So what happens here is-
- The Hacker would never receives SYN+ACK
- The webserver C.C.C.C continuously sends the SYN+ACKs for all the SYNs from A.A.A.A and never receives the ACK in return. It will fill up its memory buffers and may drop the legitimate connections.
- The result would be page cannot be displayed. If it is a windows machine there might be a possibility for a complete system crash or a BSOD. Yes, because "Windows".
- There's a very old attack called TCP flood or SYN Flood most of the today's IDS systems detects this attack easily and most web servers today have enough resources to take the beating. Well, mostly.
FIN –
Finally the FIN flag. FIN flag is used to negotiate between the peer systems that the communication is over and they can drop the connection/session gracefully. Basically, it tears down the TCP virtual connection. FIN is a 4-way handshake which appears in the last packet of a session. This can be better explained from the below figure.
I guess the picture is self explanatory. Once the source machine finishes the data transfer it sends a TCP with the FIN flag set to 1 and the destination machine acknowledges it. But this is only one way, from the picture, source machine is finished its transmission, but not the destination machine. Now the connection acts as a simplex connection. Once the destination machine finishes its transmission it also sends a TCP with FIN flag set to 1, source acknowledges it and then the connection is dropped, well, technically, the session details are flushed out from the memory. It is more like a telephone conversation.
I think the above description itself covers the example. Lets see what hackers can do.
- Exploit: I haven’t come across attacks where this flag is used, several attacks include this flag along with the others. May be there are attacks which might use this flag. It is up to you guys to figure it out. And if you find any? Do let me know in the comments.
Thanks for reading.


No comments:
Post a Comment